Whoa! The browser extension changed the rhythm of interacting with Solana. Seriously? Yes. For a lot of folks it made Web3 feel less like a maze and more like a familiar app on your desktop. My first reaction when I started following the ecosystem was cautious curiosity, not blind enthusiasm. Hmm… something about that instant wallet pop-up felt both liberating and a little alarming.
Okay, so check this out—browser extensions like Phantom act as a bridge between your browser and the Solana network, letting you sign transactions, manage tokens and NFTs, and connect to dapps without running a full node. They’re quick. They keep seed phrases offline in your device so long as you manage them well. But here’s the thing: convenience and security are in tension, and that tension matters, a lot.
What does Phantom actually do? At a basic level it stores keys, shows your balance, and signs transactions when you approve them. It lets you switch networks, request token swaps, and view NFT collections. It warns you when a dapp requests permissions. On the surface that’s straightforward. Under the hood, though, there are nuance and trade-offs that matter for daily users and builders alike, especially around permission models and phishing vectors.
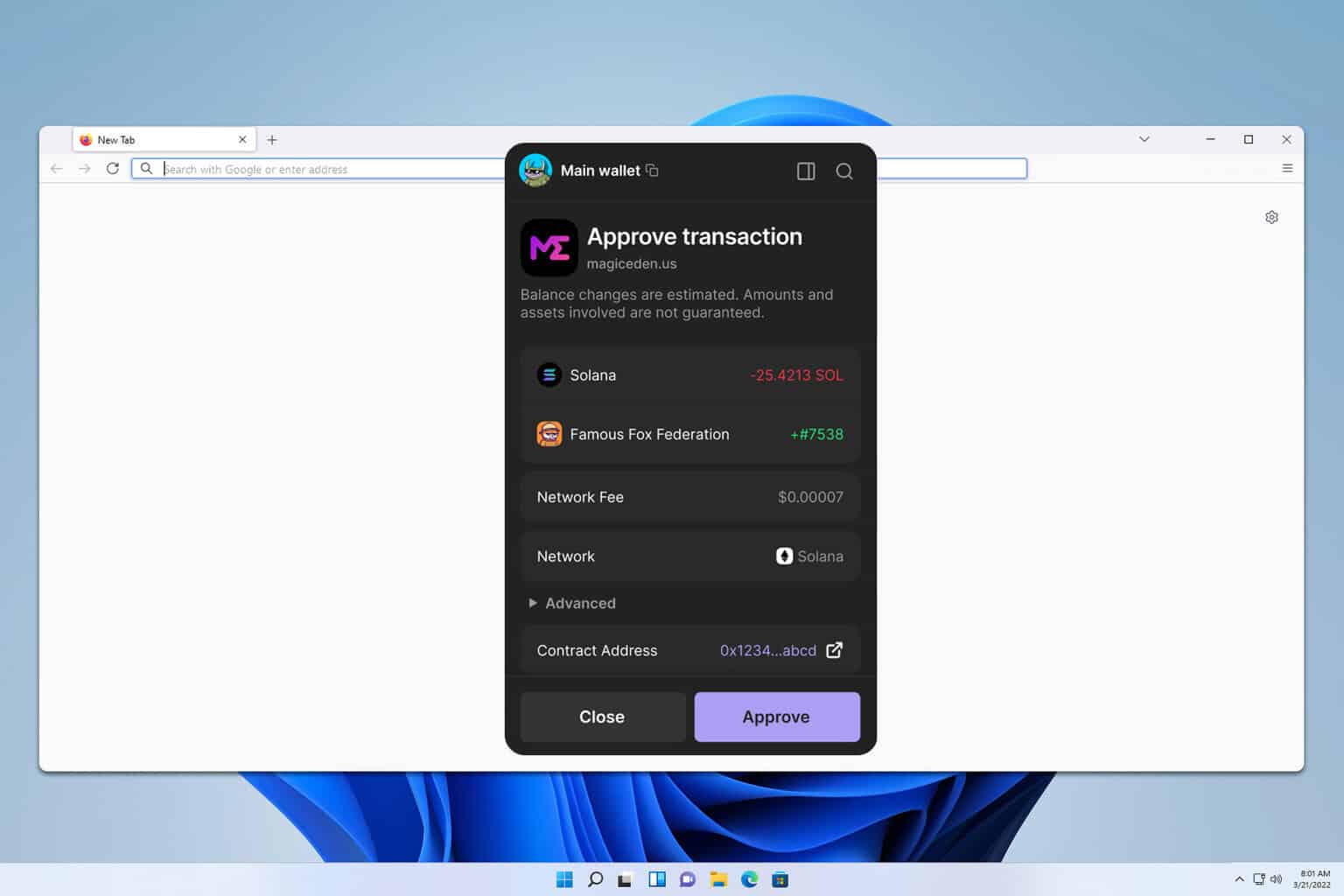
Setting up a Solana wallet extension — the human steps
Start with a fresh browser profile if you can. Seriously. Use a dedicated browser profile for crypto activities and keep other tabs separate. Create a new wallet, write down your seed phrase on paper, and store it where you won’t lose it (not on cloud notes—nope). Many people skip this step. That’s a mistake. Backups are very very important.
During setup the extension will give you a seed phrase and optionally a password for local unlocking. Use both if you want a small UX friction that helps security. On one hand passwords can be annoying; on the other, they stop casual access when someone borrows your laptop. Initially I thought the password felt redundant, but then realized how often I walk away from a machine with my session unlocked—so, yeah, re-thinking that initial meh impression.
Also, check the extension’s origin before installing. Confirm it’s from a trusted source. If you want a quick option, you can find the official Phantom installer linked here: phantom. I’m not telling you which browser to use—use what you trust—but do check the publisher details and reviews.
Daily use: small habits that reduce big risks
Don’t auto-approve sprawling permissions. When a dapp asks to “connect,” it often only needs permission to view your public address. Pause. Read. Ask why the dapp wants more. My instinct said this early on: if a site asks to “manage” tokens or sign transactions without a clear reason, walk away. Really.
Use hardware wallets where possible. Even a cheap hardware device adds a strong layer to your security model by keeping private keys offline. If you pair a hardware wallet with a browser extension, make sure the extension supports it and that you understand the signing flow. It’s a little clunky at first, though worth it for serious funds.
Beware of phishing overlays. Some scam sites mimic the look of legit dapps and will trick you into approving a malicious transaction. Trust your gut—if something feels off or the requested approval window shows unfamiliar methods, cancel and investigate. (Oh, and by the way: shortcuts and bookmarks can save you from typed-forged domains.)
Developer-facing quirks and what they mean for users
If you’re building dapps, extensions change how you design UX. They create ephemeral connected sessions that can be revoked, which is great for permission hygiene but means you must code for reconnect flows and partial approvals. On one hand this adds complexity; though actually, it forces better security practices overall.
Extensions often expose events for connection and account changes, which simplifies real-time UIs. But different wallet extensions implement these events slightly differently, so test across wallets. Compatibility testing matters more than you think—especially when you rely on permissioned signing windows that vary in language and granularity.
Testing should include negative flows. Simulate denied transactions, interrupted sessions, and reconnections. These are the conditions that reveal fragility. Seeing how a user recovers from a rejected signature often tells you more than seeing a happy-path transaction succeed.
Privacy trade-offs
Extensions by nature map your public keys to your local environment, and that can create privacy leaks if you’re not careful. Your browser history, connected dapps, and on-chain interactions can be correlated into a fingerprint. There’s no perfect privacy here; it’s a set of mitigations. Use separate wallets for different activities if you want to compartmentalize risk and reduce linkability.
Mixers and privacy-preserving services exist, though they’re legally gray in many jurisdictions and not a silver bullet. If privacy is central to your use case, you’ll need to bake that requirement into every tool you choose, and be prepared for trade-offs in convenience.
Common troubleshooting tips
Extension disappeared after an update? Check your browser’s extensions page first. Sometimes updates toggle state or require you to re-enable permissions. If the wallet can’t connect to a dapp, confirm network settings and RPC endpoints; some dapps expect specific nodes. Clearing cache occasionally helps, though use that as a last resort because it can reset sessions.
Locked out and seed phrase lost? That’s a hard stop. There is no customer support that can recover private keys. I’m biased, but this is the part that bugs me the most: human error is still the leading cause of lost funds in crypto. If you’re not comfortable with non-recoverable systems, treat small amounts as your testbed and move up as you build confidence.
FAQ
Is a browser extension wallet safe for large holdings?
Short answer: not as safe as cold storage. Extensions are convenient for daily use and interacting with dapps, but for large holdings consider hardware wallets or multisig solutions. Use the extension for convenience, but keep the bulk of your assets separated.
Can I use multiple Phantom accounts in one browser?
Yes, many extensions support multiple accounts derived from the same seed phrase or different seeds. Create separate wallets for different activities to improve privacy and reduce blast radius if an account is compromised.
What if a dapp asks to sign a strange transaction?
Pause. Verify the transaction details in the extension’s signing window. If anything is unclear—amounts, instructions, target addresses—decline and contact the dapp’s support or community channels. Better safe than sorry.
To wrap up—well, not exactly wrap up because endings can feel fake—I want you to remember one thing: convenience will always push you toward fewer safety steps, and security will nudge you toward more friction. Balancing that is the everyday work of using crypto responsibly. I’m not 100% sure there’s a single right balance for everyone, but learning the trade-offs, using hardware for serious funds, and treating permissions like a contract rather than a checkbox will get you a long way. Somethin’ to chew on.

Leave a Reply